Cangibrina is a Python-based multi platform admin dashboard finder tool which aims to obtain the location of website dashboards by using brute-force, wordlists, Google, Nmap and robots.txt.
It is multi-threaded, supports modifying your user agent, using a TOR proxy, custom dorks, Nmap integration and can use both DuckDuckGo and Google.
Cangibrina Admin Dashboard Finder Requirements
- Python 2.7
- mechanize
- PySocks
- beautifulsoup4
- html5lib
- Nmap
- TOR
Cangibrina Usage to Find Admin Dashboards
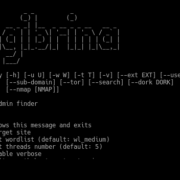
usage: cangibrina.py [-h] -u U [-w W] [-t T] [-v] [–ext EXT] [–user-agent]
[–tor] [–search] [–dork DORK] [–nmap [NMAP]]
Fast and powerful admin finder
optional arguments:
-h, –help show this help message and exit
-u U target site
-w W set wordlist (default: wl_medium)
-t T set threads number (default: 5)
-v enable verbose
–ext EXT filter path by target extension
–user-agent modify user-agent
–sub-domain search for sub domains instead of directories
–tor set TOR proxy
–search use google and duckduckgo to search
–dork DORK set custom dork
–nmap [NMAP] use nmap to scan ports and services
There are other specific tools in this area like WPScan for WordPress and DruPwn for Drupal – and in those cases the dashboard URLs are already known.
Read the rest of Cangibrina – Admin Dashboard Finder Tool now! Only available at Darknet.
Source de l’article sur Darknet