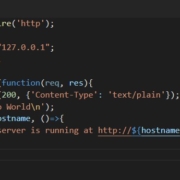
Well, the main.ts is the entry point for the Angular application. Here, we’re not able to query instances of services or get them injected because we’re outside of the Angular application. It looks like that storage object is completely decoupled from the Angular application as well, so any dependency injection you’re after you’d have to do yourself.
Also of note: while I can’t find any explicit documentation on this, Amazon’s example of this Storage class has all of its properties as static, so I’m not sure if the configuration is expecting an instance of a class at all.