Introduction
Relational databases distribute their data across many tables by normalization or according to business entities. This makes maintaining a growing database schema easier. Real-world queries often span across multiple tables, and hence joining these tables is inevitable.
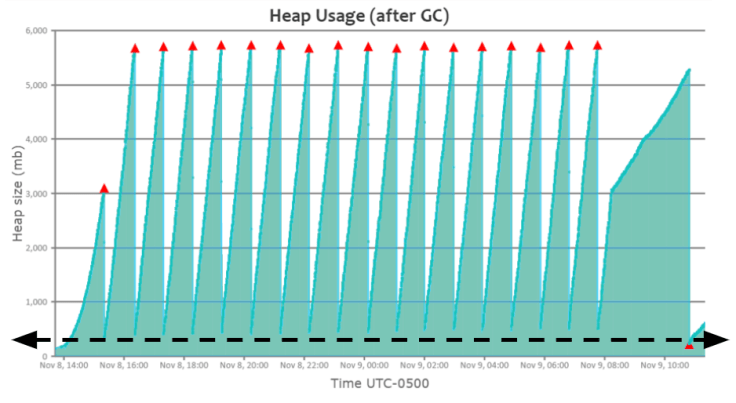
PostgreSQL uses many algorithms to join tables. In this article, we will see how joins work behind the scenes from a planner perspective and understand how to optimize them.







 Life was normal until 2020’s monstrously bad news – Covid – came around. Developers got out of bed, then marched to the office to crunch code as they always do. While inside of the office, they reviewed their goals, played with Git, interacted with their colleagues over a cup (or two) of coffee, and built products relevant to the functionality of the company. Many developers also had side-projects that they would go home and work on during their free time as their hobby.
Life was normal until 2020’s monstrously bad news – Covid – came around. Developers got out of bed, then marched to the office to crunch code as they always do. While inside of the office, they reviewed their goals, played with Git, interacted with their colleagues over a cup (or two) of coffee, and built products relevant to the functionality of the company. Many developers also had side-projects that they would go home and work on during their free time as their hobby.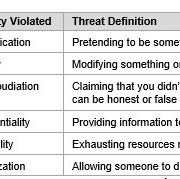
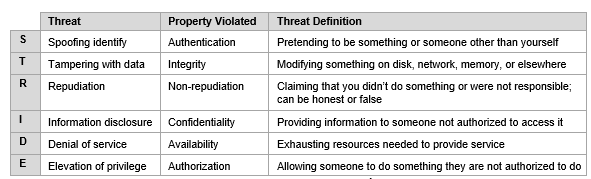

 In our
In our