Original release date: March 3, 2021 | Last revised: March 4, 2021
Summary
Cybersecurity and Infrastructure Security (CISA) partners have observed active exploitation of vulnerabilities in Microsoft Exchange Server products. Successful exploitation of these vulnerabilities allows an unauthenticated attacker to execute arbitrary code on vulnerable Exchange Servers, enabling the attacker to gain persistent system access, as well as access to files and mailboxes on the server and to credentials stored on that system. Successful exploitation may additionally enable the attacker to compromise trust and identity in a vulnerable network. Microsoft released out-of-band patches to address vulnerabilities in Microsoft Exchange Server. The vulnerabilities impact on-premises Microsoft Exchange Servers and are not known to impact Exchange Online or Microsoft 365 (formerly O365) cloud email services.
This Alert includes both tactics, techniques and procedures (TTPs) and the indicators of compromise (IOCs) associated with this malicious activity. To secure against this threat, CISA recommends organizations examine their systems for the TTPs and use the IOCs to detect any malicious activity. If an organization discovers exploitation activity, they should assume network identity compromise and follow incident response procedures. If an organization finds no activity, they should apply available patches immediately and implement the mitigations in this Alert.
Click here for IOCs in STIX format.
Technical Details
Microsoft has released out-of-band security updates to address four vulnerabilities in Exchange Server:
It is possible for an attacker, once authenticated to the Exchange server, to gain access to the Active Directory environment and download the Active Directory Database.
Tactics, Techniques and Procedures
The majority of the TTPs in this section are sourced from a blog post from Volexity, a third party cybersecurity firm. Note: the United States Government does not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply their endorsement, recommendation, or favoring by the United States Government.
Volexity has observed the following files as targets of HTTP POST requests:
/owa/auth/Current/themes/resources/logon.css/owa/auth/Current/themes/resources/owafont_ja.css/owa/auth/Current/themes/resources/lgnbotl.gif/owa/auth/Current/themes/resources/owafont_ko.css/owa/auth/Current/themes/resources/SegoeUI-SemiBold.eot/owa/auth/Current/themes/resources/SegoeUI-SemiLight.ttf/owa/auth/Current/themes/resources/lgnbotl.gif
Administrators should search the ECP server logs for the following string (or something similar):
S:CMD=Set-OabVirtualDirectory.ExternalUrl='
The logs can be found at <exchange install path>LoggingECPServer.
To determine possible webshell activity, administrators should search for aspx files in the following paths:
inetpubwwwrootaspnet_client (any .aspx file under this folder or sub folders)<exchange install path>FrontEndHttpProxyecpauth (any file besides TimeoutLogoff.aspx)<exchange install path>FrontEndHttpProxyowaauth (any file or modified file that is not part of a standard install)<exchange install path>FrontEndHttpProxyowaauthCurrent (any aspx file in this folder or subfolders)<exchange install path>FrontEndHttpProxyowaauth<folder with version number> (any aspx file in this folder or subfolders)
Administrators should search in the /owa/auth/Current directory for the following non-standard web log user-agents. These agents may be useful for incident responders to look at to determine if further investigation is necessary.
These should not be taken as definitive IOCs:
DuckDuckBot/1.0;+(+http://duckduckgo.com/duckduckbot.html)facebookexternalhit/1.1+(+http://www.facebook.com/externalhit_uatext.php)Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://www.baidu.com/search/spider.html)Mozilla/5.0+(compatible;+Bingbot/2.0;++http://www.bing.com/bingbot.htm)Mozilla/5.0+(compatible;+Googlebot/2.1;++http://www.google.com/bot.htmlMozilla/5.0+(compatible;+Konqueror/3.5;+Linux)+KHTML/3.5.5+(like+Gecko)+(Exabot-Thumbnails)Mozilla/5.0+(compatible;+Yahoo!+Slurp;+http://help.yahoo.com/help/us/ysearch/slurp)Mozilla/5.0+(compatible;+YandexBot/3.0;++http://yandex.com/bots)Mozilla/5.0+(X11;+Linux+x86_64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/51.0.2704.103+Safari/537.36
Volexity observed these user-agents in conjunction with exploitation to /ecp/ URLs:
ExchangeServicesClient/0.0.0.0python-requests/2.19.1python-requests/2.25.1
These user-agents were also observed having connections to post-exploitation web-shell access:
antSword/v2.1Googlebot/2.1+(+http://www.googlebot.com/bot.html)Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://www.baidu.com/search/spider.html)
As with the non-standard user-agents, responders can examine internet information services (IIS) logs from Exchange Servers to identify possible historical activity. Also, as with the non-standard user agents, these should not be taken as definitive IOCs:
POST /owa/auth/Current/POST /ecp/default.fltPOST /ecp/main.cssPOST /ecp/<single char>.js
Volexity has seen attackers leverage the following IP addresses. Although these are tied to virtual private servers (VPSs) servers and virtual private networks (VPNs), responders should investigate these IP addresses on their networks and act accordingly:
103.77.192[.]219104.140.114[.]110104.250.191[.]110108.61.246[.]56149.28.14[.]163157.230.221[.]198167.99.168[.]251185.250.151[.]72192.81.208[.]169203.160.69[.]66211.56.98[.]1465.254.43[.]185.2.69[.]1480.92.205[.]8191.192.103[.]43
Volexity has also provided the following YARA signatures that can be run within your network to assist in finding signs of a compromise.
1.
rule webshell_aspx_simpleseesharp : Webshell Unclassified
{
meta:
author = “threatintel@volexity.com”
date = “2021-03-01”
description = “A simple ASPX Webshell that allows an attacker to write further files to disk.”
hash = “893cd3583b49cb706b3e55ecb2ed0757b977a21f5c72e041392d1256f31166e2”
strings:
$header = “<%@ Page Language=”C#” %>”
$body = “<% HttpPostedFile thisFile = Request.Files[0];thisFile.SaveAs(Path.Combine”
condition:
$header at 0 and
$body and
filesize < 1KB
}
2.
rule webshell_aspx_reGeorgTunnel : Webshell Commodity
{
meta:
author = “threatintel@volexity.com”
date = “2021-03-01”
description = “A variation on the reGeorg tunnel webshell”
hash = “406b680edc9a1bb0e2c7c451c56904857848b5f15570401450b73b232ff38928”
reference = “https://github.com/sensepost/reGeorg/blob/master/tunnel.aspx”
strings:
$s1 = “System.Net.Sockets”
$s2 = “System.Text.Encoding.Default.GetString(Convert.FromBase64String(StrTr(Request.Headers.Get”
// a bit more experimental
$t1 = “.Split(‘|’)”
$t2 = “Request.Headers.Get”
$t3 = “.Substring(“
$t4 = “new Socket(“
$t5 = “IPAddress ip;”
condition:
all of ($s*) or
all of ($t*)
}
3
rule webshell_aspx_sportsball : Webshell Unclassified
{
meta:
author = “threatintel@volexity.com”
date = “2021-03-01”
description = “The SPORTSBALL webshell allows attackers to upload files or execute commands on the system.”
hash = “2fa06333188795110bba14a482020699a96f76fb1ceb80cbfa2df9d3008b5b0a”
strings:
$uniq1 = “HttpCookie newcook = new HttpCookie(”fqrspt”, HttpContext.Current.Request.Form”
$uniq2 = “ZN2aDAB4rXsszEvCLrzgcvQ4oi5J1TuiRULlQbYwldE=”
$var1 = “Result.InnerText = string.Empty;”
$var2 = “newcook.Expires = DateTime.Now.AddDays(”
$var3 = “System.Diagnostics.Process process = new System.Diagnostics.Process();”
$var4 = “process.StandardInput.WriteLine(HttpContext.Current.Request.Form[””
$var5 = “else if (!string.IsNullOrEmpty(HttpContext.Current.Request.Form[””
$var6 = “<input type=”submit” value=”Upload” />”
condition:
any of ($uniq*) or
all of ($var*)
}
A list of webshell hashes have also been provided by Microsoft:
b75f163ca9b9240bf4b37ad92bc7556b40a17e27c2b8ed5c8991385fe07d17d0097549cf7d0f76f0d99edf8b2d91c60977fd6a96e4b8c3c94b0b1733dc026d3e2b6f1ebb2208e93ade4a6424555d6a8341fd6d9f60c25e44afe11008f5c1aad165149e036fff06026d80ac9ad4d156332822dc93142cf1a122b1841ec8de34b5511df0e2df9bfa5521b588cc4bb5f8c5a321801b803394ebc493db1ef3c78fa14edc7770464a14f54d17f36dc9d0fe854f68b346b27b35a6f5839adf1f13f8ea811157f9c7003ba8d17b45eb3cf09bef2cecd2701cedb675274949296a6a183d1631a90eb5395c4e19c7dbcbf611bbe6444ff312eb7937e286e4637cb9e72944
Note: this is not an all-inclusive list of indicators of compromise and threat actors have been known to use short-term leased IP addresses that change very frequently. Organizations that do not locate any of the IOCs in this Alert within your network traffic, may nevertheless have been compromised. CISA recommendations following the guidance located in the Microsoft Advisory to check your servers for any signs of a compromise.
Conduct Forensic Analysis
Should your organization see evidence of compromise, your incident response should begin with conducting forensic analysis to collect artifacts and perform triage. Please see the following list of recommendations on how to conduct forensic analysis using various tools.
Although the following free tools are not endorsed by the Federal Government, incident responders commonly use them to perform forensics.
While collecting artifacts to perform triage, use processes and tools that minimize the alteration of the data being collected and that minimize impact to the operating system itself.
Ideally, during data collection, store the data on removable/external media and, when possible, run the artifact collection tools from the same media.
Key artifacts for triage that should be collected:
- Memory
- All registry hives
- All windows event logs
- All web logs
Memory can be collected with a variety of open source tools (e.g., FTK Imager by AccessData, Ram Capture by Belkasoft).
Registry and Windows Event logs can be collected with a variety of open source tools as well (e.g., FTK_Imager, Kroll Artifact Parser And Extractor [KAPE]).
Web logs can also be collected with a variety of open source tools (e.g., FTK Imager).
Windows Artifact Collection Guide
Execute the following steps in order.
1) Download the latest FTK Imager from https://accessdata.com/product-download/.
- Note: Ensure your review of and compliance with the applicable license associated with the product referenced, which can be found in the product’s User Guide. The United States Government does not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply their endorsement, recommendation, or favoring by the United States Government.
2) Collect memory from live system using FTK Imager. See Memory Capture with FTK Imager.pdf for instructions. Note: Download and copy “FTK Imager” folder to an external drive. Run FTK Imager.exe from the FTK Imager folder from external drive. Wait until memory collect is complete before proceeding to step 2.
3) Collect important system artifacts using KAPE. See KAPE Collection Procedure. Note: Download KAPE from a separate system; do not download KAPE to the target system. Run KAPE from external drive.
4) Collect disk image using FTK Imager. See Live Image with FTK Imager.pdf for instructions. Note: Run FTK Imager.exe from the “FTK Imager” folder from external drive.
Memory Capture with FTK Imager
1) Open FTK Imager. Log into the system with Administrator privileges and launch “FTK Imager.”
- Note: Ensure your review of and compliance with the applicable license associated with the product referenced. The United States Government does not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply their endorsement, recommendation, or favoring by the United States Government.
2) Open “Capture Memory. » Select “Capture Memory…” from the File menu.

Figure 1: FTK Imager – Capture Memory Command
3) Select Path and Filenames. On the window that appears, use the “Browse” button to identify the destination of the memory capture. Save the memory capture to an external device and not the main hard drive of the system. Doing so will prevent the saved file from overwriting any dataspace on the system.
- Name the destination file with a descriptive name (i.e., hostname of the system).
- Select the box “Include pagefile” and provide a name of the pagefile that is descriptive of the system.
- Do not select “Create AD1 file.”
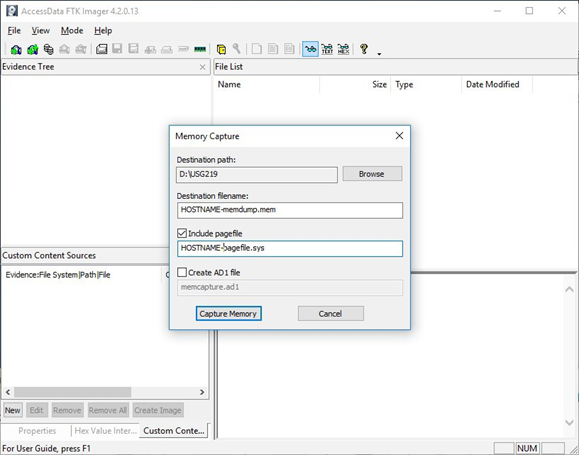
Figure 2: FTK Imager – Memory Capture
4) Capture Memory. Click on “Capture Memory” to begin the capture process. The process will take several minutes depending on the size of the pagefile and the amount of memory on the system.
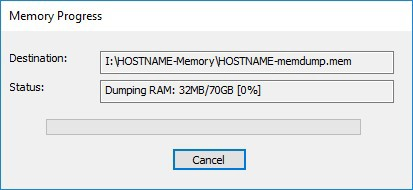
Figure 3: FTK Imager – Capture Process
KAPE Collection Procedure [1]
1) Download KAPE from https://www.kroll.com/en/services/cyber-risk/investigate-and-respond/kroll-artifact-parser-extractor-kape.
2) Disable any antivirus or host protection mechanisms that prevent execution from removable media, or data loss prevention (DLP) mechanisms that restrict utilization of removable media.
- Enable antivirus and host protection once this process is completed.
3) Unzip Kape.zip and run gkape.exe as admin from your removable media
4) Target source should be the drive on which the OS resides, typically C:.
5) Target destination should be an external drive folder, not the same drive as the Target source. If available, use an external hard drive or flash drive.
- A KAPE execution with these parameters will typically produce output artifacts with a total size of 1-25 GB.
- If you are going to be running KAPE on different machines and want to save to the same drive, ensure the Target destination folder is unique for each execution of KAPE.
6) Uncheck Flush checkbox (it is checked natively).
7) Check Add %d and Add %m checkboxes.
8) Select ALL checkboxes to ensure KAPE will target all available data that it is capable of targeting. This takes some time; use the down arrow and space bar to move through the list quickly.
9) Check Process VSCs checkbox.
10) Select Zip radio button and add Base name TargetOutput.
11) Ensure Deduplicate checkbox is checked (it is checked natively).
- At the bottom you should now see a large Current command line, similar to:
.kape.exe –tsource C: –tdest E:%d%m –tflush –target !BasicCollection,!SANS_Triage,Avast,AviraAVLogs,Bitdefender,ComboFix,ESET,FSecure,HitmanPro,Malwarebytes, McAfee,McAfee_ePO,RogueKiller,SentinelOne,Sophos,SUPERAntiSpyware,Symantec_AV_Logs,TrendMicro,VIPRE, Webroot,WindowsDefender,Ammyy,AsperaConnect,BoxDrive,CiscoJabber,CloudStorage,ConfluenceLogs,Discord, Dropbox, Exchange,ExchangeClientAccess,ExchangeTransport,FileZilla,GoogleDrive,iTunesBackup,JavaWebCache,Kaseya,LogMeIn,Notepad++, OneDrive,OutlookPSTOST,ScreenConnect,Skype,TeamViewerLogs,TeraCopy,VNCLogs, Chrome,ChromeExtensions,Edge,Firefox,InternetExplorer,WebBrowsers,ApacheAccessLog,IISLogFiles,ManageEngineLogs, MSSQLErrorLog,NGINXLogs,PowerShellConsole,KapeTriage,MiniTimelineCollection,RemoteAdmin, VirtualDisks, Gigatribe,TorrentClients,Torrents,$Boot,$J,$LogFile,$MFT,$SDS,$T,Amcache,ApplicationEvents,BCD,CombinedLogs, EncapsulationLogging,EventLogs,EventLogs-RDP,EventTraceLogs, EvidenceOfExecution,FileSystem,GroupPolicy,LinuxOnWindowsProfileFiles,LnkFilesAndJumpLists,LogFiles,MemoryFiles, MOF,OfficeAutosave,OfficeDocumentCache,Prefetch,RDPCache,RDPLogs,RecentFileCache,Recycle, RecycleBin, RecycleBinContent,RecycleBinMetadata,RegistryHives,RegistryHivesSystem,RegistryHivesUser,ScheduledTasks,SDB, SignatureCatalog,SRUM,StartupInfo,Syscache,ThumbCache,USBDevicesLogs,WBEM,WER,WindowsFirewall, WindowsIndexSearch,WindowsNotifcationsDB,WindowsTimeline,XPRestorePoints –vss –zip TargetOutput –gui
- In the bottom right corner hit the Execute! Button.
- Screenshot below shows
gkape.exe during execution, you will also see a command window execute. Note: KAPE usually takes less than 20 minutes to complete on a workstation; if it is taking significantly longer there may be an issue.

Figure 4: gkape.exe screenshot
Mitigations
CISA strongly recommends organizations read Microsoft’s advisory and security blog post for more information on how to look for this malicious activity and apply critical patches as soon as possible.
If patching is not an immediate option, there are other mitigation options available. However, these options should only be used as a temporary solution, not a replacement for patching. CISA recommends limiting or blocking external access to internet-facing Exchange Servers via the following:
- Restrict untrusted connections to port 443, or set up a VPN to separate the Exchange Server from external access; note that this will not prevent an adversary from exploiting the vulnerability if the attacker is already in your network.
- Block external access to on-premise Exchange:
CISA would like to thank Microsoft and Volexity for their contributions to this Alert.
Resources
References
Revisions
- March 3, 2021: Initial Version
This product is provided subject to this Notification and this Privacy & Use policy.
Source de l’article sur us-cert.gov
Google Will Use ‘FLoC’ for Ad Targeting Once 3rd-Party Cookies Are Dead
Actualités, Sécurité de l'information et du SI, Sécurité de l’information, Sécurité du système d’informationSignaling a major shift to its ads-driven business model, Google on Wednesday unequivocally stated it would not build alternate identifiers or tools to track users across multiple websites once it begins phasing out third-party tracking cookies from its Chrome browser by early 2022. « Instead, our web products will be powered by privacy-preserving APIs which prevent individual tracking while
Source de l’article sur The Hacker News
Le groupe APT Lazarus se tourne à présent vers l’industrie de la défense
Actualités, Sécurité de l'information et du SI, Sécurité de l’information, Sécurité du système d’informationLes chercheurs de Kaspersky ont identifié une nouvelle campagne, jusqu’alors inconnue, menée par Lazarus, un acteur APT très prolifique. Actif depuis au moins 2009, Lazarus est lié à un certain nombre de campagnes, notamment à l’encontre du marché des crypto-monnaies.
The post Le groupe APT Lazarus se tourne à présent vers l’industrie de la défense first appeared on UnderNews.
Source de l’article sur UNDERNEWS
Business optimisation architecture – Example planning optimisation
Actualités, Méthodes et organisation des process ITThe process was laid out how I’ve approached the use case and how portfolio solutions are the base for researching a generic architectural blueprint.
Source de l’article sur DZONE
Google’s FLoC Promises a Radically Different Web
Actualités, ActualitésLook up pizza recipes, and advertising will show you promotions for pizza ovens. Download a marathon training plan, and advertising will show you the latest running shoes. Buy a car, and advertising will show you adverts for other cars because no system’s perfect.
Advertising does this with a simple trick: it watches you constantly. It’s watching you right now. The web is one giant machine for making money, and you’re the fuel.
On the one hand, advertising’s insidious invasion of our privacy is enough to make you paranoid; on the other hand, I really love my pizza oven.
The largest facilitator of advertising on the web is Google Ads — reportedly worth $134.8 billion per annum; it’s Alphabet Inc’s primary source of revenue.
Last year, Google Ads announced that it would be ending its reliance on third-party cookies for delivering targeted advertising as part of a wider industry trend towards greater privacy protection for individuals. This week, we received more details confirming that Google Ads will not replace third-party cookies with comparable tracking technology.
Google Ads intends to maintain relevant advertising, without user tracking, by anonymizing your identity within a crowd. The technical term is a Federated Learning of Cohorts (FLoC), essentially Asimov’s Psychohistory, in capitalist form, some 45,000 years before Hari Seldon is due to be born.
In simplistic terms, someone who buys a pair of running shoes can reasonably be expected to be interested in GPS watches. The complexity arises when grouping becomes more complex: people who watch Netflix on a Tuesday evening purchase a particular soup brand and read the Washington Post, for example. The system requires billions of groupings that are too complex to express in English. And yet Google claims to already be making some progress.
As with any fledgling technology, the implications of its widespread adoption are unclear. FLoC is Chrome-based, so there’s the looming specter of a monopoly. Then there’s the issue of how groups are built; does Google need individual tracking to generate crowds of individuals? It’s unclear, but what is clear is that if Google succeeds — and it’s likely that it will — other networks will have no choice but to follow suit. It seems inevitable that there will be a wide-ranging impact across not just advertising but analytics and marketing as a whole.
The back door that’s being held open is one-to-one relationships. If you visit a site, that site can attempt to entice you back with targeted advertising. This means the next few years will see a growth in the number of companies developing ongoing relationships in the form of newsletters and memberships.
How ever it plays out, a fundamental change to the system that funds most of the web is certain to have a long-term impact on day-to-day user experience.
Featured image via Pexels.
Source
The post Google’s FLoC Promises a Radically Different Web first appeared on Webdesigner Depot.
Source de l’article sur Webdesignerdepot
AA21-062A: Mitigate Microsoft Exchange Server Vulnerabilities
Sécurité de l'information et du SI, Sécurité de l’information, Sécurité du système d’informationOriginal release date: March 3, 2021 | Last revised: March 4, 2021
Summary
Cybersecurity and Infrastructure Security (CISA) partners have observed active exploitation of vulnerabilities in Microsoft Exchange Server products. Successful exploitation of these vulnerabilities allows an unauthenticated attacker to execute arbitrary code on vulnerable Exchange Servers, enabling the attacker to gain persistent system access, as well as access to files and mailboxes on the server and to credentials stored on that system. Successful exploitation may additionally enable the attacker to compromise trust and identity in a vulnerable network. Microsoft released out-of-band patches to address vulnerabilities in Microsoft Exchange Server. The vulnerabilities impact on-premises Microsoft Exchange Servers and are not known to impact Exchange Online or Microsoft 365 (formerly O365) cloud email services.
This Alert includes both tactics, techniques and procedures (TTPs) and the indicators of compromise (IOCs) associated with this malicious activity. To secure against this threat, CISA recommends organizations examine their systems for the TTPs and use the IOCs to detect any malicious activity. If an organization discovers exploitation activity, they should assume network identity compromise and follow incident response procedures. If an organization finds no activity, they should apply available patches immediately and implement the mitigations in this Alert.
Click here for IOCs in STIX format.
Technical Details
Microsoft has released out-of-band security updates to address four vulnerabilities in Exchange Server:
CVE-2021-26858 and CVE-2021-27065 are similar post-authentication arbitrary write file vulnerabilities in Exchange. An attacker, authenticated either by using CVE-2021-26855 or via stolen admin credentials, could write a file to any path on the server.
CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. An attacker, authenticated either by using CVE-2021-26855 or via stolen admin credentials, could execute arbitrary code as
SYSTEMon the Exchange Server.To locate a possible compromise of these CVEs, we encourage you to read the Microsoft Advisory.
It is possible for an attacker, once authenticated to the Exchange server, to gain access to the Active Directory environment and download the Active Directory Database.
Tactics, Techniques and Procedures
The majority of the TTPs in this section are sourced from a blog post from Volexity, a third party cybersecurity firm. Note: the United States Government does not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply their endorsement, recommendation, or favoring by the United States Government.
Volexity has observed the following files as targets of
HTTP POSTrequests:/owa/auth/Current/themes/resources/logon.css/owa/auth/Current/themes/resources/owafont_ja.css/owa/auth/Current/themes/resources/lgnbotl.gif/owa/auth/Current/themes/resources/owafont_ko.css/owa/auth/Current/themes/resources/SegoeUI-SemiBold.eot/owa/auth/Current/themes/resources/SegoeUI-SemiLight.ttf/owa/auth/Current/themes/resources/lgnbotl.gifAdministrators should search the ECP server logs for the following string (or something similar):
S:CMD=Set-OabVirtualDirectory.ExternalUrl='The logs can be found at
<exchange install path>LoggingECPServer.To determine possible webshell activity, administrators should search for
aspxfiles in the following paths:inetpubwwwrootaspnet_client(any.aspxfile under this folder or sub folders)<exchange install path>FrontEndHttpProxyecpauth(any file besidesTimeoutLogoff.aspx)<exchange install path>FrontEndHttpProxyowaauth(any file or modified file that is not part of a standard install)<exchange install path>FrontEndHttpProxyowaauthCurrent(anyaspxfile in this folder or subfolders)<exchange install path>FrontEndHttpProxyowaauth<folder with version number>(anyaspxfile in this folder or subfolders)Administrators should search in the
/owa/auth/Currentdirectory for the following non-standard web log user-agents. These agents may be useful for incident responders to look at to determine if further investigation is necessary.These should not be taken as definitive IOCs:
DuckDuckBot/1.0;+(+http://duckduckgo.com/duckduckbot.html)facebookexternalhit/1.1+(+http://www.facebook.com/externalhit_uatext.php)Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://www.baidu.com/search/spider.html)Mozilla/5.0+(compatible;+Bingbot/2.0;++http://www.bing.com/bingbot.htm)Mozilla/5.0+(compatible;+Googlebot/2.1;++http://www.google.com/bot.htmlMozilla/5.0+(compatible;+Konqueror/3.5;+Linux)+KHTML/3.5.5+(like+Gecko)+(Exabot-Thumbnails)Mozilla/5.0+(compatible;+Yahoo!+Slurp;+http://help.yahoo.com/help/us/ysearch/slurp)Mozilla/5.0+(compatible;+YandexBot/3.0;++http://yandex.com/bots)Mozilla/5.0+(X11;+Linux+x86_64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/51.0.2704.103+Safari/537.36Volexity observed these user-agents in conjunction with exploitation to
/ecp/URLs:ExchangeServicesClient/0.0.0.0python-requests/2.19.1python-requests/2.25.1These user-agents were also observed having connections to post-exploitation web-shell access:
antSword/v2.1Googlebot/2.1+(+http://www.googlebot.com/bot.html)Mozilla/5.0+(compatible;+Baiduspider/2.0;++http://www.baidu.com/search/spider.html)As with the non-standard user-agents, responders can examine internet information services (IIS) logs from Exchange Servers to identify possible historical activity. Also, as with the non-standard user agents, these should not be taken as definitive IOCs:
POST /owa/auth/Current/POST /ecp/default.fltPOST /ecp/main.cssPOST /ecp/<single char>.jsVolexity has seen attackers leverage the following IP addresses. Although these are tied to virtual private servers (VPSs) servers and virtual private networks (VPNs), responders should investigate these IP addresses on their networks and act accordingly:
103.77.192[.]219104.140.114[.]110104.250.191[.]110108.61.246[.]56149.28.14[.]163157.230.221[.]198167.99.168[.]251185.250.151[.]72192.81.208[.]169203.160.69[.]66211.56.98[.]1465.254.43[.]185.2.69[.]1480.92.205[.]8191.192.103[.]43Volexity has also provided the following YARA signatures that can be run within your network to assist in finding signs of a compromise.
rule webshell_aspx_simpleseesharp : Webshell Unclassified
{
meta:
author = “threatintel@volexity.com”
date = “2021-03-01”
description = “A simple ASPX Webshell that allows an attacker to write further files to disk.”
hash = “893cd3583b49cb706b3e55ecb2ed0757b977a21f5c72e041392d1256f31166e2”
strings:
$header = “<%@ Page Language=”C#” %>”
$body = “<% HttpPostedFile thisFile = Request.Files[0];thisFile.SaveAs(Path.Combine”
condition:
$header at 0 and
$body and
filesize < 1KB
}
2.
rule webshell_aspx_reGeorgTunnel : Webshell Commodity
{
meta:
author = “threatintel@volexity.com”
date = “2021-03-01”
description = “A variation on the reGeorg tunnel webshell”
hash = “406b680edc9a1bb0e2c7c451c56904857848b5f15570401450b73b232ff38928”
reference = “https://github.com/sensepost/reGeorg/blob/master/tunnel.aspx”
strings:
$s1 = “System.Net.Sockets”
$s2 = “System.Text.Encoding.Default.GetString(Convert.FromBase64String(StrTr(Request.Headers.Get”
// a bit more experimental
$t1 = “.Split(‘|’)”
$t2 = “Request.Headers.Get”
$t3 = “.Substring(“
$t4 = “new Socket(“
$t5 = “IPAddress ip;”
condition:
all of ($s*) or
all of ($t*)
}
3
rule webshell_aspx_sportsball : Webshell Unclassified
{
meta:
author = “threatintel@volexity.com”
date = “2021-03-01”
description = “The SPORTSBALL webshell allows attackers to upload files or execute commands on the system.”
hash = “2fa06333188795110bba14a482020699a96f76fb1ceb80cbfa2df9d3008b5b0a”
strings:
$uniq1 = “HttpCookie newcook = new HttpCookie(”fqrspt”, HttpContext.Current.Request.Form”
$uniq2 = “ZN2aDAB4rXsszEvCLrzgcvQ4oi5J1TuiRULlQbYwldE=”
$var1 = “Result.InnerText = string.Empty;”
$var2 = “newcook.Expires = DateTime.Now.AddDays(”
$var3 = “System.Diagnostics.Process process = new System.Diagnostics.Process();”
$var4 = “process.StandardInput.WriteLine(HttpContext.Current.Request.Form[””
$var5 = “else if (!string.IsNullOrEmpty(HttpContext.Current.Request.Form[””
$var6 = “<input type=”submit” value=”Upload” />”
condition:
any of ($uniq*) or
all of ($var*)
}
A list of webshell hashes have also been provided by Microsoft:
b75f163ca9b9240bf4b37ad92bc7556b40a17e27c2b8ed5c8991385fe07d17d0097549cf7d0f76f0d99edf8b2d91c60977fd6a96e4b8c3c94b0b1733dc026d3e2b6f1ebb2208e93ade4a6424555d6a8341fd6d9f60c25e44afe11008f5c1aad165149e036fff06026d80ac9ad4d156332822dc93142cf1a122b1841ec8de34b5511df0e2df9bfa5521b588cc4bb5f8c5a321801b803394ebc493db1ef3c78fa14edc7770464a14f54d17f36dc9d0fe854f68b346b27b35a6f5839adf1f13f8ea811157f9c7003ba8d17b45eb3cf09bef2cecd2701cedb675274949296a6a183d1631a90eb5395c4e19c7dbcbf611bbe6444ff312eb7937e286e4637cb9e72944Note: this is not an all-inclusive list of indicators of compromise and threat actors have been known to use short-term leased IP addresses that change very frequently. Organizations that do not locate any of the IOCs in this Alert within your network traffic, may nevertheless have been compromised. CISA recommendations following the guidance located in the Microsoft Advisory to check your servers for any signs of a compromise.
Conduct Forensic Analysis
Should your organization see evidence of compromise, your incident response should begin with conducting forensic analysis to collect artifacts and perform triage. Please see the following list of recommendations on how to conduct forensic analysis using various tools.
Although the following free tools are not endorsed by the Federal Government, incident responders commonly use them to perform forensics.
While collecting artifacts to perform triage, use processes and tools that minimize the alteration of the data being collected and that minimize impact to the operating system itself.
Ideally, during data collection, store the data on removable/external media and, when possible, run the artifact collection tools from the same media.
Key artifacts for triage that should be collected:
Memory can be collected with a variety of open source tools (e.g., FTK Imager by AccessData, Ram Capture by Belkasoft).
Registry and Windows Event logs can be collected with a variety of open source tools as well (e.g., FTK_Imager, Kroll Artifact Parser And Extractor [KAPE]).
Web logs can also be collected with a variety of open source tools (e.g., FTK Imager).
Windows Artifact Collection Guide
Execute the following steps in order.
1) Download the latest FTK Imager from https://accessdata.com/product-download/.
2) Collect memory from live system using FTK Imager. See Memory Capture with FTK Imager.pdf for instructions. Note: Download and copy “FTK Imager” folder to an external drive. Run FTK Imager.exe from the FTK Imager folder from external drive. Wait until memory collect is complete before proceeding to step 2.
3) Collect important system artifacts using KAPE. See KAPE Collection Procedure. Note: Download KAPE from a separate system; do not download KAPE to the target system. Run KAPE from external drive.
4) Collect disk image using FTK Imager. See Live Image with FTK Imager.pdf for instructions. Note: Run FTK Imager.exe from the “FTK Imager” folder from external drive.
Memory Capture with FTK Imager
1) Open FTK Imager. Log into the system with Administrator privileges and launch “FTK Imager.”
2) Open “Capture Memory. » Select “Capture Memory…” from the File menu.
Figure 1: FTK Imager – Capture Memory Command
3) Select Path and Filenames. On the window that appears, use the “Browse” button to identify the destination of the memory capture. Save the memory capture to an external device and not the main hard drive of the system. Doing so will prevent the saved file from overwriting any dataspace on the system.
Figure 2: FTK Imager – Memory Capture
4) Capture Memory. Click on “Capture Memory” to begin the capture process. The process will take several minutes depending on the size of the pagefile and the amount of memory on the system.
Figure 3: FTK Imager – Capture Process
KAPE Collection Procedure [1]
1) Download KAPE from https://www.kroll.com/en/services/cyber-risk/investigate-and-respond/kroll-artifact-parser-extractor-kape.
2) Disable any antivirus or host protection mechanisms that prevent execution from removable media, or data loss prevention (DLP) mechanisms that restrict utilization of removable media.
3) Unzip Kape.zip and run gkape.exe as admin from your removable media
4) Target source should be the drive on which the OS resides, typically C:.
5) Target destination should be an external drive folder, not the same drive as the Target source. If available, use an external hard drive or flash drive.
6) Uncheck Flush checkbox (it is checked natively).
7) Check Add %d and Add %m checkboxes.
8) Select ALL checkboxes to ensure KAPE will target all available data that it is capable of targeting. This takes some time; use the down arrow and space bar to move through the list quickly.
9) Check Process VSCs checkbox.
10) Select Zip radio button and add Base name TargetOutput.
11) Ensure Deduplicate checkbox is checked (it is checked natively).
gkape.exeduring execution, you will also see a command window execute. Note: KAPE usually takes less than 20 minutes to complete on a workstation; if it is taking significantly longer there may be an issue.Figure 4: gkape.exe screenshot
Mitigations
CISA strongly recommends organizations read Microsoft’s advisory and security blog post for more information on how to look for this malicious activity and apply critical patches as soon as possible.
If patching is not an immediate option, there are other mitigation options available. However, these options should only be used as a temporary solution, not a replacement for patching. CISA recommends limiting or blocking external access to internet-facing Exchange Servers via the following:
/owa/.Restrict external access to Exchange Admin Center (EAC) aka Exchange Control Panel (ECP) URL:
/ecp/.CISA would like to thank Microsoft and Volexity for their contributions to this Alert.
Resources
References
Revisions
This product is provided subject to this Notification and this Privacy & Use policy.
Source de l’article sur us-cert.gov
Flint Group transforme ses achats avec les solutions SAP Ariba
Actualités, ERP & Applications, SAPSAP SE (NYSE : SAP) a annonce que le groupe Flint, l’un des plus grands fournisseurs d’encres, de presses d’impression numérique et d’autres produits destinés à l’industrie de l’impression et de l’emballage, a centralisé et digitalisé ses processus d’achats indirects et d’achats de services grâce aux solutions SAP Ariba. L’entreprise a ainsi gagné en efficacité, réduit ses coûts et amélioré le contrôle de ses dépenses.
Les solutions SAP Ariba ont remplacé les processus procure-to-pay jusque-là manuels de Flint Group, qui nécessitaient des commandes individuelles pour chaque fournisseur. Grâce à une plate-forme unique et unifiée dans le cloud, l’entreprise a standardisé son processus d’achat dans l’ensemble de son entreprise et a rendu les actes d’achats, la facturation et la comptabilité plus faciles et plus transparents pour les employés, les fournisseurs, les managers et le service comptabilité.
« Nous avons considérablement amélioré l’expérience d’achat de nos employés et l’efficacité des processus grâce à notre migration vers le cloud et à la mise en œuvre des solutions SAP Ariba », a déclaré Arno de Groot, vice-président, Procurement Packaging, Flint Group. « De plus, grâce à un système d’achat unifié complet, nous avons une meilleure visibilité sur les dépenses, ce qui nous permet de prendre des décisions d’achat plus éclairées et a un effet positif sur nos résultats ».
Le groupe Flint opère dans plus de 130 centres répartis sur six continents et travaille avec un réseau vaste et diversifié de fournisseurs pour satisfaire ses clients. Avant la mise en œuvre des solutions SAP Ariba, la gestion des achats indirects du groupe était complexe et chronophage. Le manque de transparence des dépenses et l’incohérence des données se traduisaient par une vision incomplète des coûts et une incapacité à prendre des décisions d’achat bien informées. Maintenant que les solutions SAP Ariba sont en place et intégrées à l’application SAP ERP de l’entreprise, le groupe Flint a pu :
Pour en savoir plus sur la transformation digitale du groupe Flint, cliquez ici.
The post Flint Group transforme ses achats avec les solutions SAP Ariba appeared first on SAP France News.
Source de l’article sur sap.com
Hackers Now Hiding ObliqueRAT Payload in Images to Evade Detection
Actualités, Sécurité de l'information et du SI, Sécurité de l’information, Sécurité du système d’informationCybercriminals are now deploying remote access Trojans (RATs) under the guise of seemingly innocuous images hosted on infected websites, once again highlighting how threat actors quickly change tactics when their attack methods are discovered and exposed publicly.
New research released by Cisco Talos reveals a new malware campaign targeting organizations in South Asia that utilize malicious
Source de l’article sur The Hacker News
8 Best Premium Stock Image Sites for 2021
Actualités, ActualitésLast month we looked at the 10 Best Free Stock Image Sites for 2021, and this month we’re focusing on the premium end of the market.
Paying for stock doesn’t guarantee that you’re getting a higher quality product than the free alternative, but the higher quality product is rarely free.
Ultimately, the right image is the right image, regardless of price. These are the best places to start your search in 2021.
1. Stocksy
Stocksy is a tremendous site with a slight edge to its imagery. There’s a certain cool vibe to the images featured on Stocksy. If you’re looking for a stock image that doesn’t look like a stock image, this is a great place to begin. Its prices range from around $15 for a small web image to $1000s for the image’s exclusive use.
2. EyeEm
EyeEm is a great source of editorial-style images. It has some excellent categories that are geared towards finding images instead of categorizing the collection. Pricing starts at $35 per image, with discounts for image packs. EyeEm has recently introduced the option to book a photoshoot — for clients ready to pay for custom images.
3. Getty Images
It’s impossible to make a list of stock image sites without including Getty Images. The stock behemoth not only has one of the largest collections of stock images but owns several subsidiaries. Loved by news media for its comprehensive coverage, if you’re looking for a particular stock image, try Getty. Getty’s a mid-price supplier with prices for small images starting at around $75.
4. Death to Stock
Death to Stock is all about leveraging the stock industry to fund photographers. These are photographs that photography professionals admire; there’s no filler whatsoever. Subscriptions for creative professionals start from $33/month. There are 100+ new images added to the collection monthly, meaning it’s still small, but if you want something truly authentic, consider Death to Stock.
5. Cavan Images
Cavan’s focus is on building a broad range of photographers, which has produced an outstanding set of diverse images. The curated collections, which are more editorial than commercial, are powerful. Cavan also offers a great support service in case you need help tracking down a particular image. Prices vary but start from $50.
6. Offset & Shutterstock
Shutterstock is one of the best-known stock collections on the web, with over 300 million images. Offset is a subsidiary of the much larger Shutterstock; it’s a high-end version of Shutterstock, with slightly elevated prices to reflect the higher quality. Shutterstock prices start around $2.50/image, Offset’s start around $300; that’s the price you pay for having someone pre-vet your options.
7. Westend61
Westend61 has a smaller collection, but its images are all consistently high quality. Westend61 is particularly useful for designing banner images because the images are very commercial, with authentic-looking people and lots of eye contact. Prices per image start at approximately $25.
8. iStock
iStock was originally independent but was bought by Getty. iStock offers both credit, and subscription options starting around $2.50/image. Although you won’t find everything you’ll find on the larger Getty site, it’s worth checking to see if the image you want is here.
Source
The post 8 Best Premium Stock Image Sites for 2021 first appeared on Webdesigner Depot.
Source de l’article sur Webdesignerdepot
Oubliez les mots de passe grâce à la YubiKey et à Microsoft Azure Active Directory
Actualités, Sécurité de l'information et du SI, Sécurité de l’information, Sécurité du système d’informationYubico, spécialiste des clés de sécurité pour l’authentification matérielle, annonce une étape importante dans l’évolution de l’authentification moderne. L’authentification sans mot de passe proposée par la YubiKey est désormais disponible pour tous les utilisateurs d’Azure Active Directory (Azure AD) de Microsoft.
The post Oubliez les mots de passe grâce à la YubiKey et à Microsoft Azure Active Directory first appeared on UnderNews.
Source de l’article sur UNDERNEWS